Good morning, security gang! Welcome to another episode of the CyberHub Podcast. I’m still on the road this week, pre-recording in the early hours to ensure you stay informed on the latest in cybersecurity. While I miss the comforts of my studio and a proper double espresso, I’ve got a packed episode for you.
Today’s discussion spans Apple zero-day fixes, espionage campaigns, ransomware operations, and more. Let’s dive in!
Apple Fixes Two Critical Zero-Day Vulnerabilities
Apple has addressed two critical zero-day vulnerabilities in macOS that were actively exploited. The flaws, tracked as CVE-2024-44308 and CVE-2024-44309, were found in macOS's JavaScriptCore and could enable remote code execution and cross-site scripting via malicious web content.
Key Updates:
Patches released for macOS Sequoia, iOS 17.7.2, and iPadOS 18.1.1.
Discovered by Google’s Threat Analysis Group, Apple has not disclosed further exploit details.
Apple’s zero-day vulnerability count has dropped significantly compared to last year.
Update your Apple devices immediately to mitigate risk.
China-Linked Espionage Group Targets Global Telecoms
A new Advanced Persistent Threat (APT), "Liminal Panda," has been identified by CrowdStrike as targeting telecom entities in South Asia and Africa. This group demonstrates deep expertise in telecommunications, leveraging custom tools like Sigtran Translator and PingPong to exfiltrate call metadata and subscriber data.
Key Highlights:
Methods include weak password exploitation and sophisticated command-and-control setups.
Similarities noted with earlier threat actor "Light Basin."
The attack underscores the growing threat of Chinese state-sponsored cyber espionage.
Policy Response: Experts call for enhanced U.S. public-private collaboration and increased investment in threat intelligence and infrastructure resilience.
Cargill Data Breach Lawsuit Dismissed
The U.S. Circuit Court of Appeals upheld the dismissal of a lawsuit against Cargill stemming from the 2021 ransomware attack on Kronos. While plaintiffs argued payroll errors caused by the breach violated labor laws, courts determined Cargill had compensated employees fairly post-incident. This case illustrates the prolonged operational and legal consequences of data breaches, even when victims are compensated.
Ford Investigates Hacking Claims
A hacker claimed to breach Ford’s systems, but the company quickly clarified that the issue involved a third-party supplier and publicly available data. Ford confirmed no proprietary or customer data was compromised, resolving the matter within 24 hours.
Oracle and Progress Vulnerability Patches
Oracle released a patch for CVE-2024-21287, an actively exploited vulnerability in its Agile Product Lifecycle Management software. Meanwhile, CISA added three vulnerabilities to its catalog, including flaws in Palo Alto Networks and Progress Kemp LoadMaster, urging immediate patching. Apply updates to affected systems to prevent potential exploitation.
Ransomware Operations Expanding
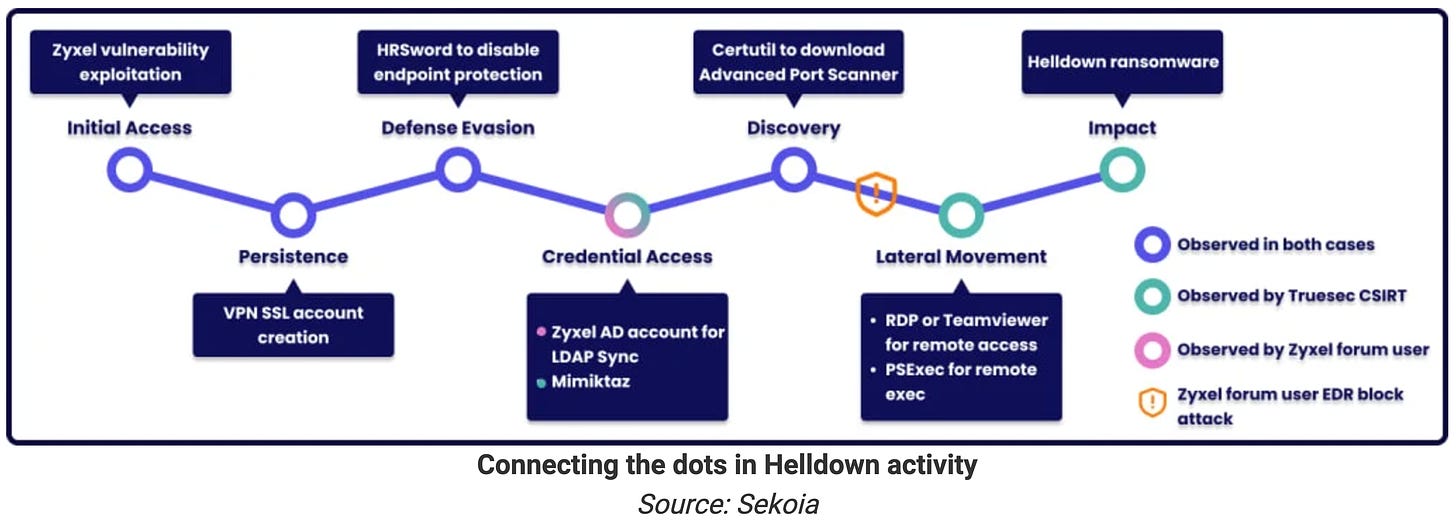
The “Helldown” ransomware group continues to target U.S. and European firms using vulnerabilities in Zyxel firewalls. Despite their amateur approach, the group’s ability to infiltrate corporate networks and steal data remains concerning.
Recommendations:
Regularly update firewall firmware.
Conduct thorough vulnerability scans across corporate networks.
NSO Group Under Scrutiny in WhatsApp Lawsuit
Revelations from court filings in the WhatsApp-NSO Group lawsuit expose NSO's deep operational involvement in its Pegasus spyware. Contrary to NSO’s claims, evidence shows they managed the infrastructure, facilitated spyware deployment, and exfiltrated data for their clients. This case sheds light on the blurred lines between tech providers and state actors in cyber surveillance.
Action Items for Security Teams
Patch Critical Vulnerabilities: Ensure all Apple, Oracle, Progress Kemp, and Palo Alto systems are updated to their latest secure versions.
Strengthen Telecom Security: Proactively monitor telecom systems for espionage activity, focusing on weak passwords and atypical protocol activity.
Review Third-Party Risks: Ford’s experience highlights the importance of assessing third-party supplier security.
Reassess Ransomware Readiness: Implement robust endpoint protection and maintain regular backups to minimize ransomware risks.
Enhance Collaboration: Advocate for stronger public-private partnerships in threat intelligence sharing and infrastructure resilience.
Conclusion
That’s it for today’s CyberHub Podcast! For a full summary and additional resources, subscribe to [my Substack](https://jamesazer.substack.com) for free. You’ll find detailed summaries, action items, and my latest articles, including this week’s focus on identity security best practices.
Stay cyber-safe, and we’ll catch you tomorrow for more insights and updates!
✅ Story Links:
https://www.cybersecuritydive.com/news/cargill-kronos-discrimination-suit-dismissed/732942/
https://thehackernews.com/2024/11/china-backed-hackers-leverage-sigtran.html
https://www.securityweek.com/ford-says-leaked-data-comes-from-supplier-and-is-not-sensitive/
https://www.securityweek.com/oracle-patches-exploited-agile-plm-zero-day/
https://www.bankinfosecurity.com/us-agencies-urged-to-combat-growing-chinese-cyberthreat-a-26858
https://therecord.media/nso-group-whatsapp-case-documents
🔔 Subscribe now for the latest insights from industry leaders, in-depth analyses, and real-world strategies to secure your digital world. https://www.youtube.com/@TheCyberHubPodcast/?sub_confirmation=1
✅ Important Links to Follow:
👉Substack:
👉Listen here: https://linktr.ee/cyberhubpodcast
✅ Stay Connected With Us.
👉Facebook: https://www.facebook.com/CyberHubpodcast/
👉LinkedIn: https://www.linkedin.com/company/cyberhubpodcast/
👉Twitter (X): https://twitter.com/cyberhubpodcast
👉Instagram: https://www.instagram.com/cyberhubpodcast
✅ For Business Inquiries: info@cyberhubpodcast.com
=============================
✅ About The CyberHub Podcast.
The Hub of the Infosec Community.
Our mission is to provide substantive and quality content that’s more than headlines or sales pitches. We want to be a valuable source to assist those cybersecurity practitioners in their mission to keep their organizations secure.
Tune in to our podcast Monday through Thursday at 9AM EST for the latest news.















Share this post