Tackling Identity Security, Avoiding the Hype: Challenges and Best Practices
Mastering Identity Security: How to Safeguard Human and Non-Human Identities in a Complex Digital World, the guide you need.
When we say identity is the new perimeter In today’s world we mean it and identity security is no longer just about protecting usernames and passwords. The scope of identity has expanded beyond humans to include non-human entities such as applications, APIs, containers, and cloud services. As cybersecurity practitioners, we face an unprecedented challenge: managing and securing identity across diverse platforms and environments, each with unique vulnerabilities and complexities.
In this article, I’ll delve into the core challenges of identity security across multiple identity platforms and non-human identities and propose actionable best practices to address these challenges.
The Challenges of Identity Security
1. Fragmentation Across Identity Platforms
Organizations often operate with multiple identity providers (IdPs) such as Microsoft Azure AD, Okta, Google Workspace, and AWS IAM. Each platform comes with its own management interfaces, security settings, and capabilities. The lack of a unified view creates blind spots, making it harder to detect and respond to suspicious activity, adding more screens to watch and creating a complex environment to manage.
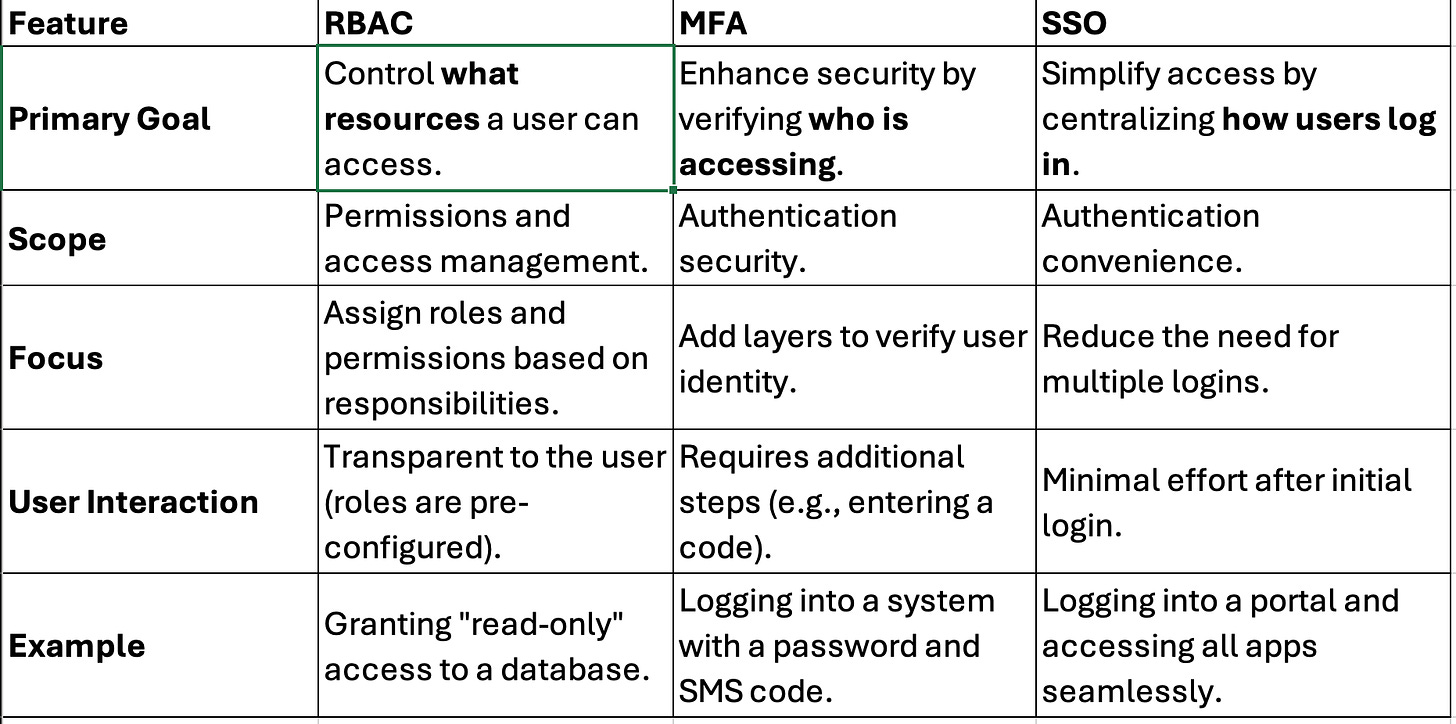
Key Differences
How They Work Together
These concepts often complement each other:
RBAC ensures that users can only access resources relevant to their role.
MFA adds a layer of security, ensuring the user logging in is indeed who they claim to be.
SSO simplifies the authentication process across multiple systems, making it easier for users while leveraging MFA for enhanced security.
Together, they form a comprehensive framework for identity and access management. However, that doesn’t come with some key challenges.
Inconsistent Policies: Policies like password complexity, multi-factor authentication (MFA), and role-based access control (RBAC) vary across platforms.
Limited Interoperability: Many platforms have proprietary implementations, making integration complex.
Increased Attack Surface: More platforms mean more entry points for attackers to exploit.
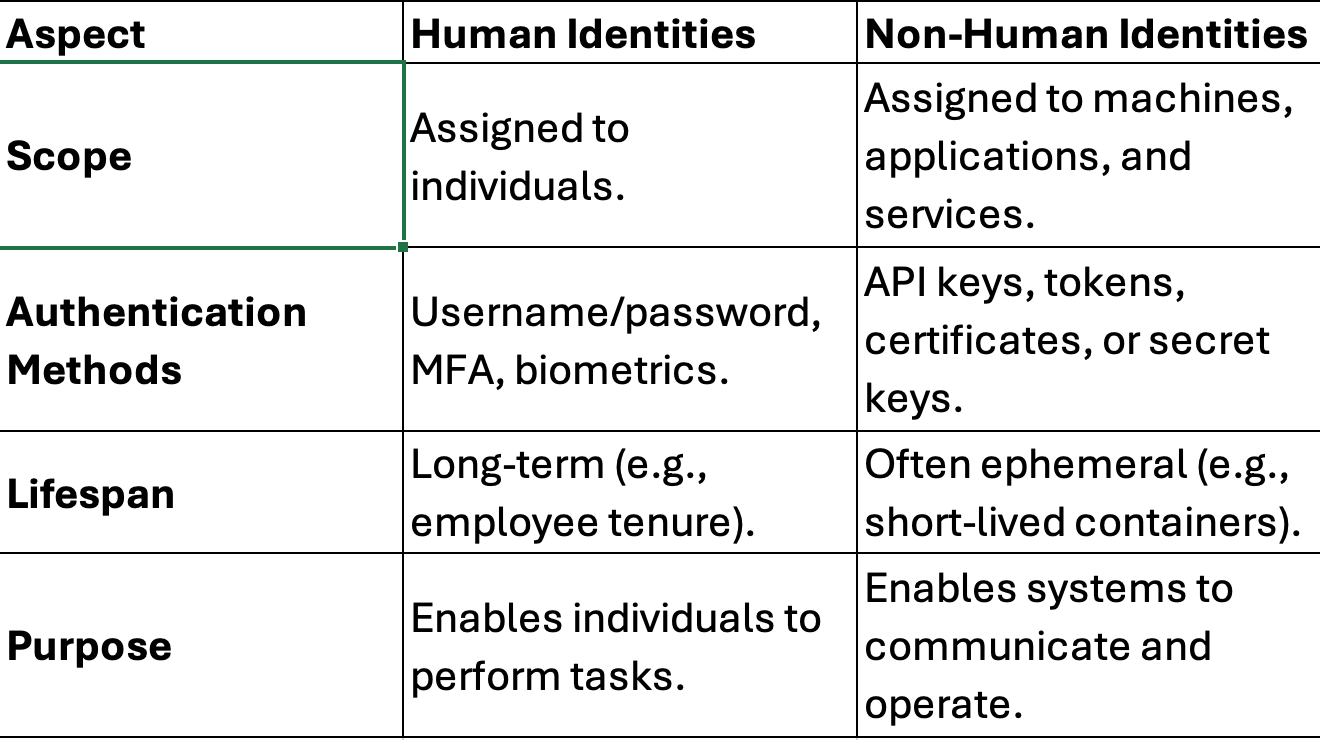
2. Human vs. Non-Human Identity
Human and Non-Human Identities are critical concepts in identity and access management (IAM), each serving distinct purposes in business operations. Traditional identity security focuses on humans, but modern environments require securing machine identities such as APIs, containers, and IoT devices. Unlike human identities, machine identities scale exponentially and often have higher privileges.
Below is an overview of what they are, how they are used, and their role in business environments:
Human Identities
Definition: Human identities refer to the digital identities assigned to individuals within an organization, such as employees, contractors, customers, or partners. These identities enable people to authenticate themselves and access the systems, applications, and data they need for their roles.
Examples of Human Identities:
An employee logging into their workstation using a username and password.
A customer accessing an online portal with an email address and MFA.
A third-party contractor using an organization’s VPN for specific project tasks.
How Businesses Use Human Identities:
Workforce Access:
Employees use their identities to access internal systems like HR software, email, and collaboration tools (e.g., Microsoft Teams, Google Workspace).
Role-Based Access Control (RBAC) ensures employees only access data relevant to their job.
Customer Engagement:
Businesses assign customer identities to provide personalized services, such as e-commerce accounts or online banking portals.
Customer IAM (CIAM) systems handle authentication, privacy, and user preferences.
Vendor and Partner Collaboration:
Partners and contractors are given limited, role-specific access to company systems to collaborate on projects securely.
Business Value:
Ensures secure, efficient workforce operations.
Enhances customer experience with personalized, secure services.
Facilitates safe collaboration with external parties.
Non-Human Identities
Definition: Non-human identities are digital identities assigned to software, applications, devices, and services that require authentication and authorization to perform tasks. These identities often involve APIs, cloud workloads, IoT devices, and service accounts.
Examples of Non-Human Identities:
An API key used to connect a payment gateway to an e-commerce platform.
A Kubernetes container requesting access to a database.
IoT devices in a smart factory communicating with a control system.
How Businesses Use Non-Human Identities:
Application-to-Application Communication:
APIs authenticate using tokens or keys to securely exchange data between applications (e.g., CRM integrating with ERP systems).
Microservices in a containerized environment authenticate with each other using certificates.
Cloud and DevOps Automation:
Virtual machines, containers, and serverless functions in cloud environments use non-human identities to manage workloads and resources dynamically.
CI/CD pipelines use service accounts to deploy applications securely.
IoT and Operational Technology (OT):
IoT devices (e.g., sensors, cameras) use non-human identities to send data to central systems in manufacturing, healthcare, or energy sectors.
Infrastructure Management:
Non-human identities control access for infrastructure automation tools (e.g., Ansible, Terraform) to manage configurations and deployments.
Business Value:
Facilitates seamless, automated communication between systems and services.
Enhances efficiency in cloud and DevOps environments.
Powers modern IoT and OT systems in manufacturing, healthcare, and beyond.
Key Differences and Relationship
Challenges and Best Practices
Human Identities:
Challenges:
Weak passwords and lack of MFA can lead to credential theft.
Over-provisioned access rights create security risks.
Best Practices:
Implement MFA for all human identities.
Regularly review and audit access rights.
Non-Human Identities:
Challenges:
Managing and rotating API keys, tokens, and certificates.
Monitoring the ephemeral nature of cloud workloads and containers.
Best Practices:
Use automated tools like Hashi Corp Vault for secret management.
Adopt Zero Trust principles for service-to-service communication.
Both human and non-human identities are integral to modern business operations. While human identities drive collaboration and customer engagement, non-human identities enable seamless automation, cloud efficiency, and IoT innovation. Businesses must manage and secure both types of identities effectively to mitigate risks, ensure compliance, and maintain operational excellence.
3. Cloud, Containers, and APIs
Cloud environments, container orchestration platforms (e.g., Kubernetes), and APIs introduce new layers of complexity. Each layer requires its own identity model and security controls.
Key Challenges:
Cloud Provider-Specific Controls: Each cloud provider (AWS, Azure, GCP) has unique identity constructs, making multi-cloud environments harder to secure.
Container Ephemeral Nature: Containers are short-lived, and traditional identity and access management (IAM) solutions struggle to adapt.
API Security: APIs often lack adequate authentication and authorization, becoming a favorite target for attackers.
Best Practices to Solve Identity Challenges
1. Centralize Identity Management
Adopt a unified identity platform or federate identities across systems using standards like SAML, OAuth, and OpenID Connect. This allows centralized policy enforcement and visibility.
Actions to Take:
Use identity orchestration tools like Ping Identity or Okta for consistent management.
Implement a single sign-on (SSO) strategy to reduce password sprawl and improve user experience.
2. Embrace Zero Trust Principles
Shift away from perimeter-based security and implement identity-centric security. Assume breach and verify every access request based on the least privilege principle.
Actions to Take:
Implement MFA for all identities—human and non-human.
Use conditional access policies to adapt authentication requirements based on risk (e.g., device health, geolocation, or time of access).
Employ Just-in-Time (JIT) access for machine identities, providing temporary access tokens instead of long-lived credentials.
3. Automate Identity Lifecycle Management
Automation is crucial to handle the scale and complexity of identities, especially for non-human entities.
Actions to Take:
Use tools like Hashi Corp Vault for secret management and automatic key rotation.
Integrate identity platforms with CI/CD pipelines to provision and deprovision access for containers and APIs dynamically.
4. Strengthen API Security
Secure APIs by embedding authentication and authorization mechanisms directly into their design.
Actions to Take:
Use OAuth 2.0 with access tokens and scopes to limit API access.
Employ API gateways like Kong or AWS API Gateway to enforce consistent security policies.
Regularly scan APIs for vulnerabilities using tools like Postman or OWASP ZAP.
5. Monitor and Respond to Identity Threats
Continuous monitoring and real-time alerts are essential to detect identity-related anomalies early.
Actions to Take:
Deploy User and Entity Behavior Analytics (UEBA) to detect unusual patterns.
Use a Security Information and Event Management (SIEM) system to correlate identity events across platforms.
Enable logging for non-human entities and regularly audit their activity.
6. Establish a Governance Framework
Develop clear policies and frameworks to manage identity security holistically.
Actions to Take:
Conduct regular identity audits to identify unused or over-privileged accounts.
Align identity security practices with compliance requirements like GDPR, CCPA, and NIST guidelines.
Train staff on identity security best practices, ensuring they understand the risks and their roles.
As the identity landscape continues to evolve, cybersecurity practitioners must adopt adaptive and scalable strategies to secure identities across diverse platforms and environments. By centralizing identity management, embracing Zero Trust, automating identity lifecycles, and strengthening API and non-human identity security, we can reduce the attack surface and better protect our organizations.
Identity security is no longer just an IT problem—it’s a foundational element of business resilience. By implementing these best practices, we can ensure that identity remains a strong defense line in our ever-changing threat landscape.
Creating a role of Identity Analyst and Identity engineers will be the normal for organization within the next several years as the focus shifts to identity and more tooling will be required to manage it all. What are some of your best practices on identity management, comment below and join the conversation to be featured on the show.