Good morning, Security Gang! It’s great to be back with you this Monday morning as we dive into a short but impactful week in cybersecurity ahead of the Thanksgiving holiday. This week, we’re tackling some of the latest developments in cybersecurity, showcasing both the maturity of the industry and the challenges that remain.
Let’s kick things off with a coffee cup cheer and dive right in.
Palo Alto Zero-Day Vulnerability Dispute
The week began with the ongoing controversy surrounding Palo Alto’s critical zero-day vulnerabilities (CVE-2024-0012 and CVE-2024-9474). These were exploited in tandem in an operation dubbed "Lunar Peak." While Palo Alto claims limited exploitation of firewall management interfaces, nonprofit Shadow Server argues otherwise, estimating nearly 2,000 devices were compromised.
Key points:
Palo Alto released a patch and SysAdmin updated its KEV catalog.
Shadow Server's credibility suggests the issue might be more extensive.
The incident underscores challenges in vulnerability and patch management, emphasizing the balancing act between mitigating risks and minimizing downtime.
Nearest Neighbor Wi-Fi Attack by Fancy Bear (APT28)
In a highly complex attack method, Russian GRU-linked Fancy Bear executed a "nearest neighbor" attack, breaching an enterprise Wi-Fi network by daisy-chaining connections from nearby buildings.
Key takeaways:
The attack exploited dual-homed devices and zero-day vulnerabilities.
MFA initially thwarted direct access, but attackers pivoted through creative lateral moves.
While such attacks are rare, they showcase the ingenuity of nation-state actors.
China-Linked Linux Espionage Campaign
China-backed Galicium is targeting Linux systems with novel malware, including Wolfbane and Firewood. This campaign extends the group's espionage activities to East Asia and the Middle East.
Highlights:
The malware focuses on cyber espionage, exfiltrating sensitive system information.
Tools include Linux versions of previously identified backdoors for Windows systems.
The attacks leverage unknown vulnerabilities in web applications.
Microlise Ransomware Attack
UK-based vehicle tracking provider Microlise confirmed a ransomware attack that disrupted critical services for prison vans and courier vehicles. The SafeBay ransomware group claims to have stolen 1.2 TB of data.
Key details:
Data theft affected services like tracking systems and alarms.
The company has restored services and informed international authorities.
Claims of data stolen might be exaggerated, but the breach highlights vulnerabilities in IoT-heavy industries.
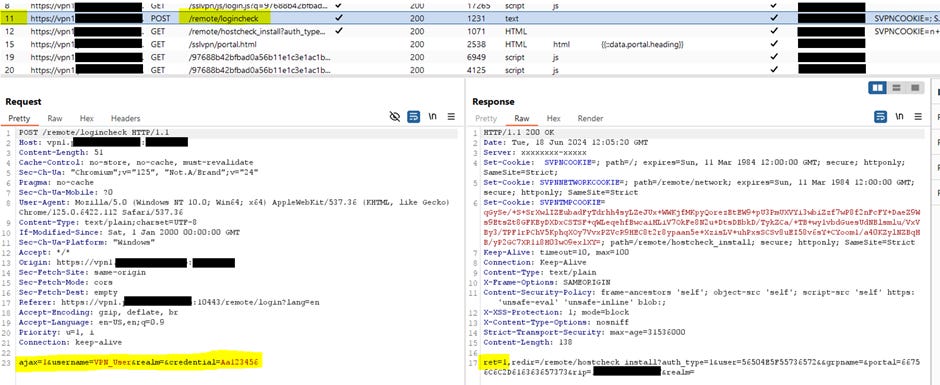
Fortinet VPN Design Flaw
A design flaw in Fortinet’s VPN login mechanism allows attackers to conceal successful brute force attempts, giving defenders a false sense of security.
Insights:
The issue lies in logging only failed authentication attempts, not successful ones.
Attackers can confirm credentials without alerting admins.
Fortinet has yet to respond, emphasizing the need for vigilance in monitoring authentication logs.
Courtesy of Pentera
Microsoft Disrupts Onyx Phishing Service
Microsoft disrupted the Onyx phishing-as-a-service operation and identified its operator, Abinub Nadi, an Egyptian cybercriminal. Despite the takedown, Nadi remains at large.
Key points:
Onyx offered phishing kits starting at $150/month.
The operation supported advanced phishing techniques like adversary-in-the-middle attacks.
Microsoft’s action disrupted 240 domains linked to the operation.
SMS Blaster Arrest in Thailand
Thai police arrested a Chinese man using an SMS blaster to send phishing texts to Bangkok residents at a rate of 100,000 messages per hour.
Details:
The device mimicked legitimate rewards messages to steal credit card data.
The suspect coordinated the scam with accomplices through private Telegram channels.
Authorities are pursuing other gang members.
North Korea’s Fake IT Worker Scam
North Korea’s fake IT worker scam, designed to evade financial sanctions, is expanding globally. The scheme targets businesses in Australia, the US, the UK, and beyond.
Key insights:
Fake workers impersonate legitimate freelancers to funnel earnings to the regime.
The scam highlights the creative lengths adversaries go to bypass economic restrictions.
TSA Facial Recognition Debate
Twelve US senators raised concerns about TSA’s widespread use of facial recognition technology without proper privacy audits or assessments of its accuracy.
Key points:
Facial recognition is being rolled out to 430 airports nationwide.
Lawmakers questioned its necessity given existing CAT-1 scanners.
The debate underscores growing privacy and surveillance concerns.
Action List for Cybersecurity Professionals
Review firewall configurations and patch policies in light of the Palo Alto vulnerabilities.
Reassess Wi-Fi security protocols to mitigate risks from nearest neighbor attacks.
Evaluate Linux system defenses for potential exposure to new malware strains like Wolfbane.
Conduct audits of IoT systems to address vulnerabilities highlighted by the Microlease breach.
Monitor VPN authentication logs for anomalies in successful brute force attempts.
Educate staff on phishing risks to combat advanced phishing-as-a-service models.
Implement SMS filtering tools to detect and block mass phishing campaigns.
Screen IT hires thoroughly to prevent fake worker scams.
Engage in the privacy debate by advocating for transparency in biometric technology use.
Stay cyber-safe, and enjoy the Thanksgiving holiday!
✅ Story Links:
https://therecord.media/china-hackers-linux-malware-target
https://www.securityweek.com/microlise-confirms-data-breach-as-ransomware-group-steps-forward/
https://www.securityweek.com/microsoft-disrupts-onnx-phishing-service-names-its-operator/
https://www.securityweek.com/north-korea-deploying-fake-it-workers-in-china-russia-other-countries/
https://therecord.media/tsa-facial-recognition-tech-senators-call-for-audits
🔔 Subscribe now for the latest insights from industry leaders, in-depth analyses, and real-world strategies to secure your digital world. https://www.youtube.com/@TheCyberHubPodcast/?sub_confirmation=1
✅ Important Links to Follow:
👉Substack:
👉Listen here: https://linktr.ee/cyberhubpodcast
✅ Stay Connected With Us.
👉Facebook: https://www.facebook.com/CyberHubpodcast/
👉LinkedIn: https://www.linkedin.com/company/cyberhubpodcast/
👉Twitter (X): https://twitter.com/cyberhubpodcast
👉Instagram: https://www.instagram.com/cyberhubpodcast
✅ For Business Inquiries: info@cyberhubpodcast.com
=============================
✅ About The CyberHub Podcast.
The Hub of the Infosec Community.
Our mission is to provide substantive and quality content that’s more than headlines or sales pitches. We want to be a valuable source to assist those cybersecurity practitioners in their mission to keep their organizations secure.
Tune in to our podcast Monday through Thursday at 9AM EST for the latest news.














Share this post