Good morning, Security Gang! Today’s episode of the CyberHelp Podcast dives into several critical cybersecurity developments. From a ransomware attack on supply chain provider Blue Yonder disrupting food availability to sophisticated Chinese APT campaigns and notable data breach fines, this episode is packed with key insights to help you stay vigilant. As Thanksgiving approaches, these stories highlight the importance of robust cybersecurity measures to mitigate risks in an ever-evolving threat landscape.
Story Highlights
Blue Yonder Supply Chain Attack
Arizona-based supply chain software provider Blue Yonder suffered a ransomware attack on November 21. Blue Yonder supports critical industries, including food supply, warehousing, and logistics. Major customers like Starbucks, Morrison’s, Sainsbury’s, and Kroger reported disruptions in scheduling and operations. The attack underscores the fragility of supply chain redundancies and the importance of disaster recovery (DR) and business continuity (BC) planning. Organizations are urged to evaluate their response plans to avoid similar disruptions.
Salt Typhoon and Chinese Cyber Espionage
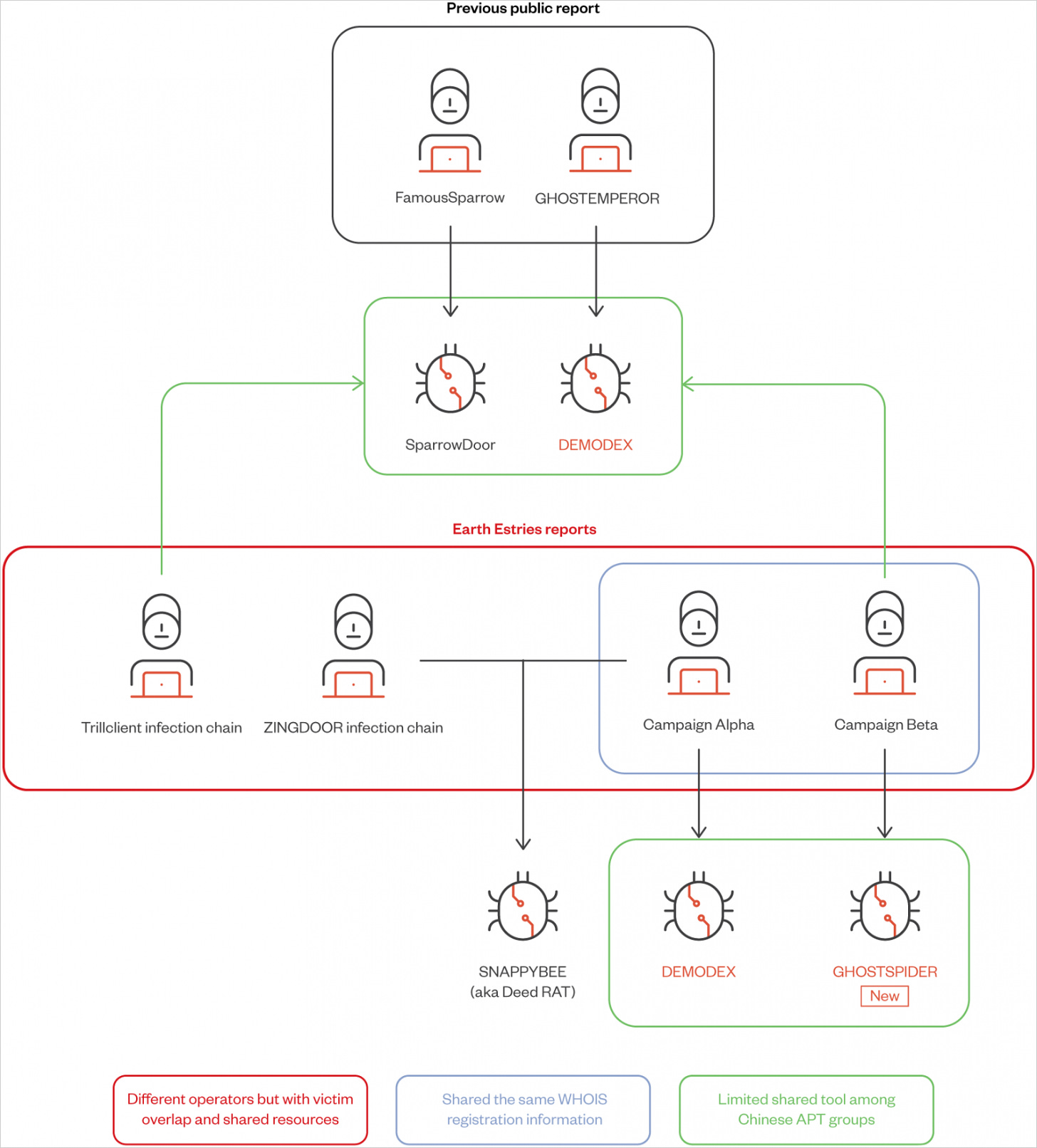
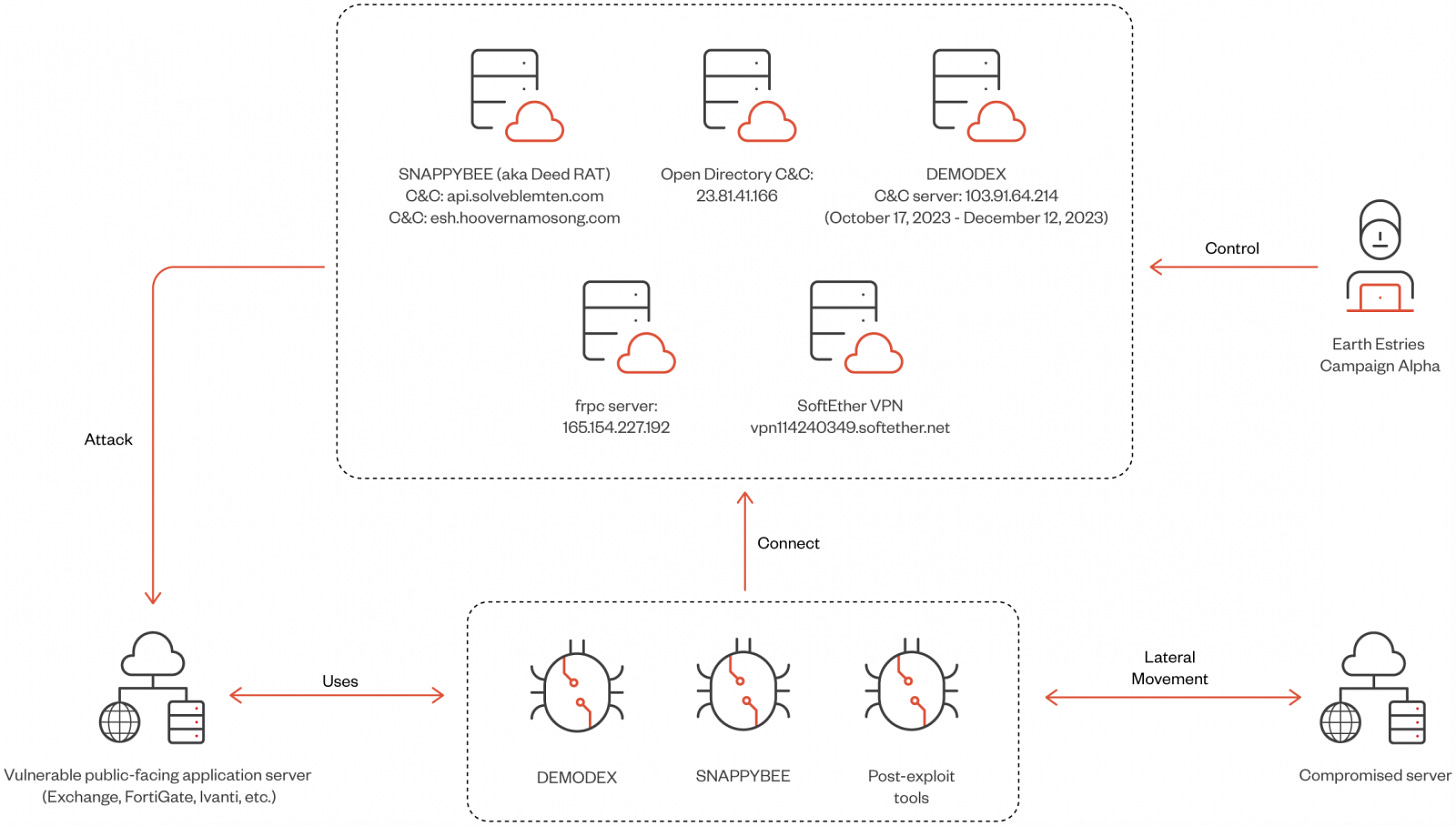
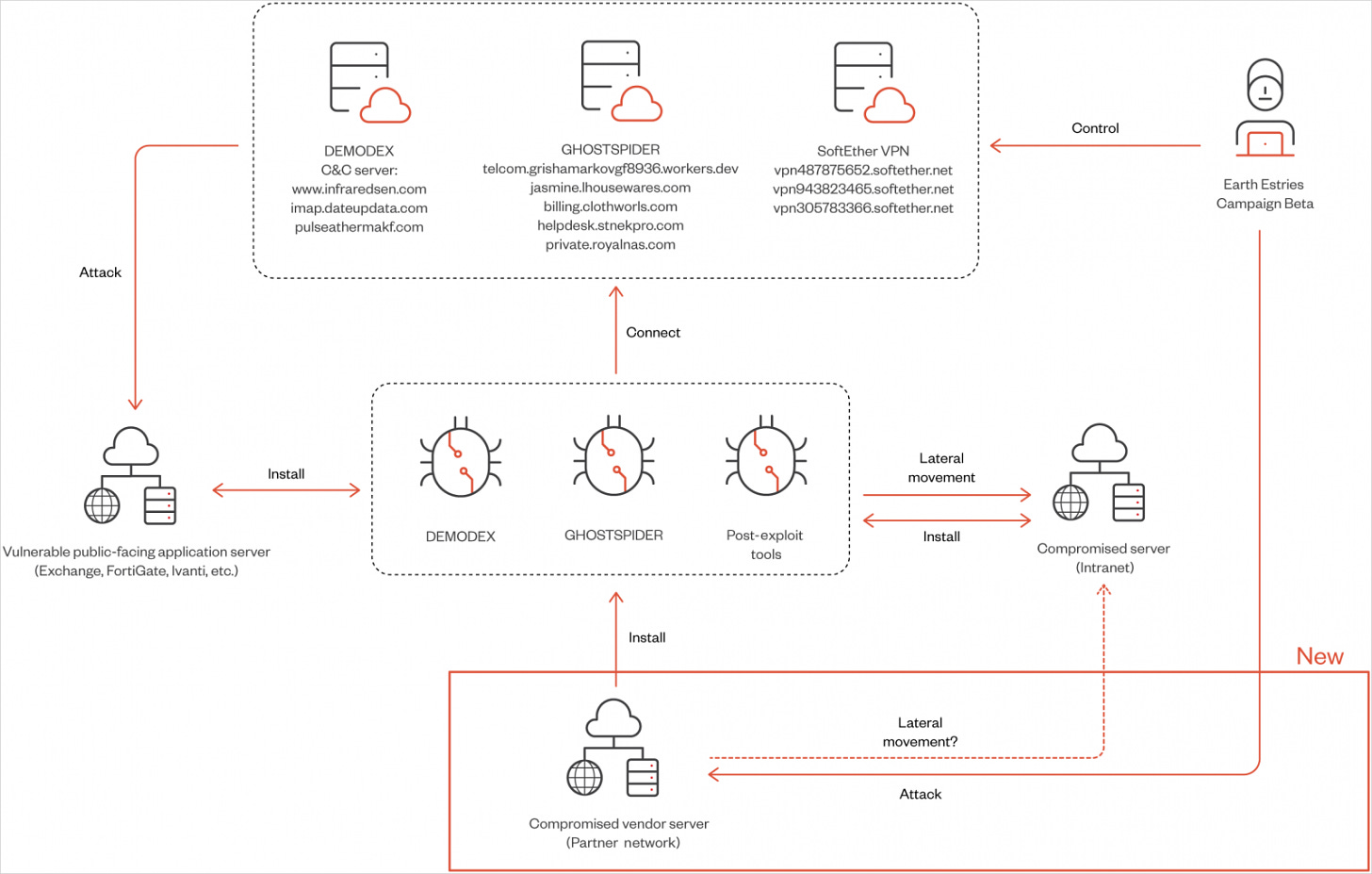
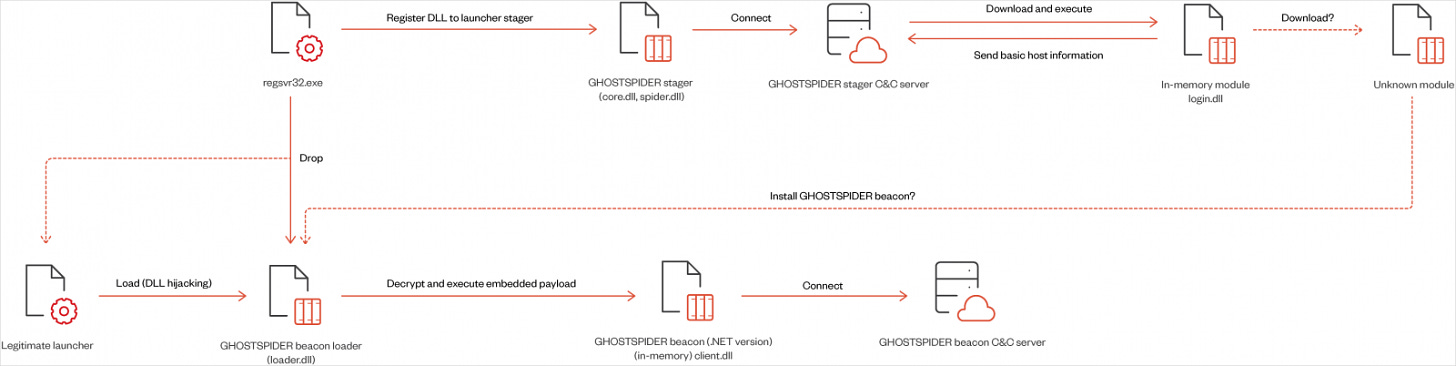
Chinese APT group Salt Typhoon, identified as the actor behind recent telecom breaches in the U.S., deployed a sophisticated backdoor called "Ghost Spider." This malware chain exploited multiple CVEs across Fortinet, Microsoft ProxyLogon, and Sophos products. Notable victims included telcos like AT&T, T-Mobile, and Verizon, as well as government officials in Washington, D.C. The campaign demonstrates the ongoing evolution of Chinese cyber espionage targeting critical infrastructure.
Initial access is achieved through the exploitation of vulnerable public-facing endpoints, using exploits for the following flaws:
CVE-2023-46805, CVE-2024-21887 (Ivanti Connect Secure VPN)
CVE-2023-48788 (Fortinet FortiClient EMS)
CVE-2022-3236 (Sophos Firewall)
CVE-2021-26855, CVE-2021-26857, CVE-2021-26858, CVE-2021-27065 (Microsoft Exchange – ProxyLogon)
All Images are courtesy of Trend Micro.
Other tools used by Salt Typhoon
Apart from GhostSpider, Salt Typhoon relies on a set of proprietary tools and ones shared among other Chinese threat actors that enable them to conduct complex, multi-stage espionage operations extending from edge devices to cloud environments.
SNAPPYBEE: Modular backdoor (also called Deed RAT) used for long-term access and espionage. It supports functionalities like data exfiltration, system monitoring, and executing attacker commands.
MASOL RAT: Cross-platform backdoor initially identified targeting Southeast Asian governments. It focuses on Linux servers, enabling remote access and command execution.
DEMODEX: Rootkit used to maintain persistence on compromised systems. It leverages anti-analysis techniques and ensures the attacker remains undetected for extended periods.
SparrowDoor: Backdoor providing remote access capabilities, used for lateral movement and establishing C&C communication.
CrowDoor: Backdoor used for espionage, particularly targeting government and telecommunications entities, focused on stealth and data exfiltration.
ShadowPad: Malware shared among Chinese APT groups, used for espionage and system control. It acts as a modular platform to deploy various malicious plugins.
NeoReGeorg: Tunneling tool used for creating covert communication channels, allowing attackers to bypass network defenses and control compromised systems.
frpc: Open-source reverse proxy tool used for creating secure connections to C&C servers, enabling data exfiltration and remote command execution.
Cobalt Strike: Commercially available penetration testing tool co-opted by attackers to create beacons for lateral movement, privilege escalation, and remote control.
All in all, Salt Typhoon's arsenal is extensive, including widely used tools that can make attribution complicated when researchers have limited visibility.
All Images are courtesy of Trend Micro.
The backdoor supports the following commands:
Upload: Loads a malicious module into memory for execution of specific attacker-controlled tasks.
Create: Activates the loaded module by initializing necessary resources for its operation.
Normal: Executes the primary function of the loaded module, such as data exfiltration or system manipulation.
Close: Removes the active module from memory to minimize traces and free system resources.
Update: Adjusts the malware's behavior, such as communication intervals, to remain stealthy and effective.
Heartbeat: Maintains periodic communication with the C&C server to confirm the system is still accessible.
The structure of these commands gives the backdoor versatility and allows Salt Typhoon to adjust their attack as needed depending on the victim's network and defenses.
All Images are courtesy of Trend Micro.
Exploitation of Array Networks’ VPN Products
CISA issued warnings about a critical vulnerability (CVE-2023-28461) in Array Networks’ VPN products. Exploited in the wild, this flaw enables unauthenticated remote code execution, endangering systems still running unpatched versions. Companies using affected versions must patch immediately to prevent data breaches.
Geico and Travelers Data Breach Fines
The New York Attorney General fined Geico and Travelers a combined $11 million for failing to secure sensitive customer data, including driver’s license numbers. The breaches, exploited for unemployment fraud during the pandemic, highlight the necessity of implementing multi-factor authentication (MFA) and timely detection protocols.
On Monday, the New York OAG and DFS announced a $9.75 million settlement (PDF) with Geico and a $1.55 million settlement (PDF) with Travelers. The two auto insurance companies agreed to review and improve their cybersecurity practices through comprehensive information security programs, data inventories, reasonable authentication procedures, logging and monitoring systems, and improved threat response procedures.
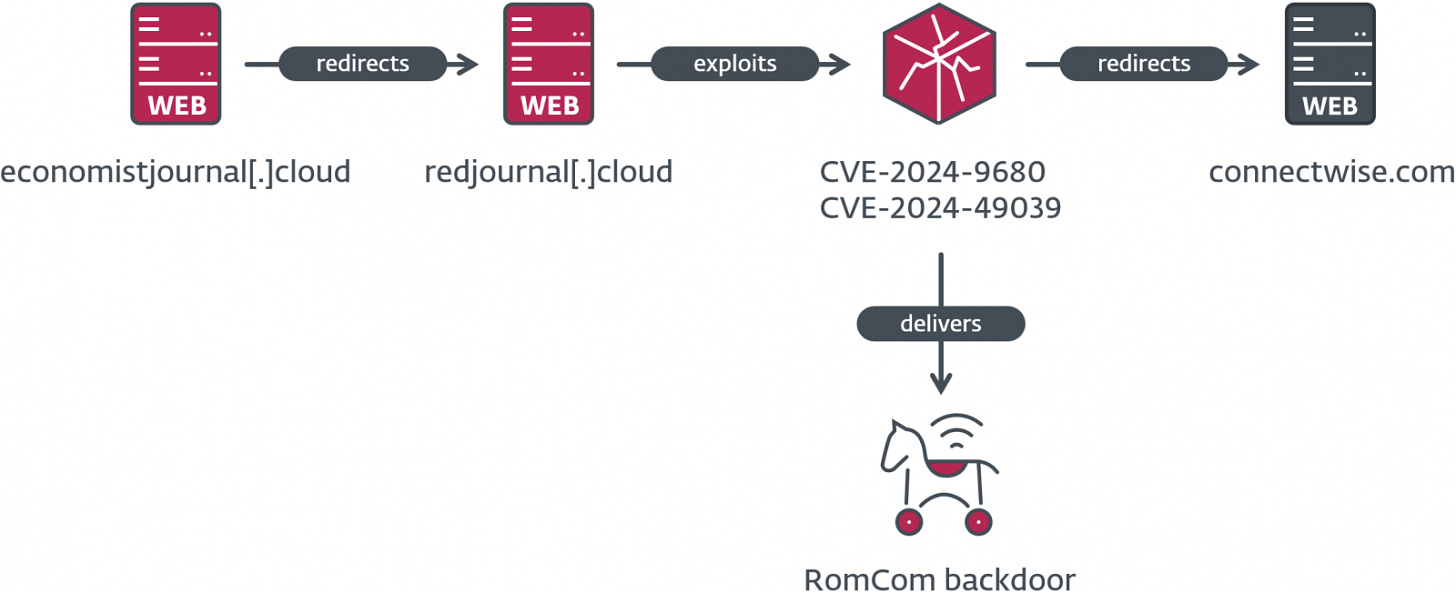
RomCom Zero-Day Exploits Targeting Firefox and Tor Browsers
The RomCom cybercrime group leveraged two zero-day vulnerabilities to target Firefox and Tor browser users in Europe and North America. By chaining a use-after-free flaw in Firefox and a privilege escalation vulnerability in Windows Task Scheduler, attackers gained remote access and executed payloads. Mozilla and Microsoft have since patched these vulnerabilities, emphasizing the need for rapid patch management.
RomCom attack flow (ESET)
SCADA System Vulnerabilities in MyPro
Industrial automation systems like MyPro SCADA are under threat from critical vulnerabilities, including OS command injection and missing authentication. Patching SCADA systems is complex, requiring planned outages and vendor involvement, making these vulnerabilities particularly concerning for industrial sectors.
Kansas Cybersecurity Marketer’s Illegal Tactics
Nicholas Michael Kloster, a Kansas City resident, attempted to promote his cybersecurity services by illegally breaching networks. His actions, which included hacking a health club and nonprofit organization, have led to federal charges. This story serves as a cautionary tale against unethical marketing practices in the cybersecurity field.
QNAP Security Bulletins
QNAP released patches for critical vulnerabilities affecting its products, including server-side request forgery and missing authentication flaws. Users must prioritize applying these patches to secure their devices and prevent unauthorized access.
Key Takeaways for Businesses and Individuals
Enhance Resilience: Develop robust DR and BC plans to mitigate disruptions during attacks.
Patch Management: Regularly update software and systems to address known vulnerabilities.
Implement MFA: Strengthen security postures by requiring multi-factor authentication for access.
Monitor Supply Chains: Evaluate the cybersecurity measures of third-party vendors.
Educate Staff: Build organizational awareness about threats and appropriate response actions.
Action List:
Evaluate Supply Chain Risks: Conduct a review of vendor cybersecurity practices and redundancy plans.
Patch Now: Update affected systems, including VPNs, browsers, and SCADA software.
Implement MFA: Enforce MFA across all sensitive platforms.
Subscribe to Alerts: Follow advisories from CISA and other authorities for real-time updates.
Secure SCADA Systems: Schedule downtime to address critical vulnerabilities.
Monitor Activity: Leverage threat intelligence to detect lateral movement or post-compromise actions.
Closing Note
As we head into Thanksgiving, let’s stay proactive and prepared. Stay cyber safe, enjoy your coffee, and remember, cybersecurity is a collective effort. Join us tomorrow for our final show of the week before the holiday!
✅ Story Links:
https://www.securityweek.com/starbucks-grocery-stores-hit-by-blue-yonder-ransomware-attack/
https://www.securityweek.com/new-york-fines-geico-and-travelers-11-million-over-data-breaches/
https://www.securityweek.com/recent-zyxel-firewall-vulnerability-exploited-in-ransomware-attacks/
https://www.securityweek.com/vulnerabilities-expose-myscada-mypro-systems-to-remote-hacking/
https://therecord.media/uk-minister-criticized-hyperbolic-russia
🔔 Subscribe now for the latest insights from industry leaders, in-depth analyses, and real-world strategies to secure your digital world. https://www.youtube.com/@TheCyberHubPodcast/?sub_confirmation=1
✅ Important Links to Follow:
👉Substack:
👉Listen here: https://linktr.ee/cyberhubpodcast
✅ Stay Connected With Us.
👉Facebook: https://www.facebook.com/CyberHubpodcast/
👉LinkedIn: https://www.linkedin.com/company/cyberhubpodcast/
👉Twitter (X): https://twitter.com/cyberhubpodcast
👉Instagram: https://www.instagram.com/cyberhubpodcast
✅ For Business Inquiries: info@cyberhubpodcast.com
=============================
✅ About The CyberHub Podcast.
The Hub of the Infosec Community.
Our mission is to provide substantive and quality content that’s more than headlines or sales pitches. We want to be a valuable source to assist those cybersecurity practitioners in their mission to keep their organizations secure.
Tune in to our podcast Monday through Thursday at 9AM EST for the latest news.














Share this post