Substack Update: The Importance of CISO Tenure
James, the host, highlights the latest Substack article focusing on the critical role of Chief Information Security Officers (CISOs) in building a resilient cybersecurity posture.
Action Points:
Leadership Engagement: Business leaders should prioritize the selection and support of CISOs to enhance cybersecurity resilience.
Read and Support: Subscribe to the Substack and support the podcast for more insightful articles and exclusive merchandise.
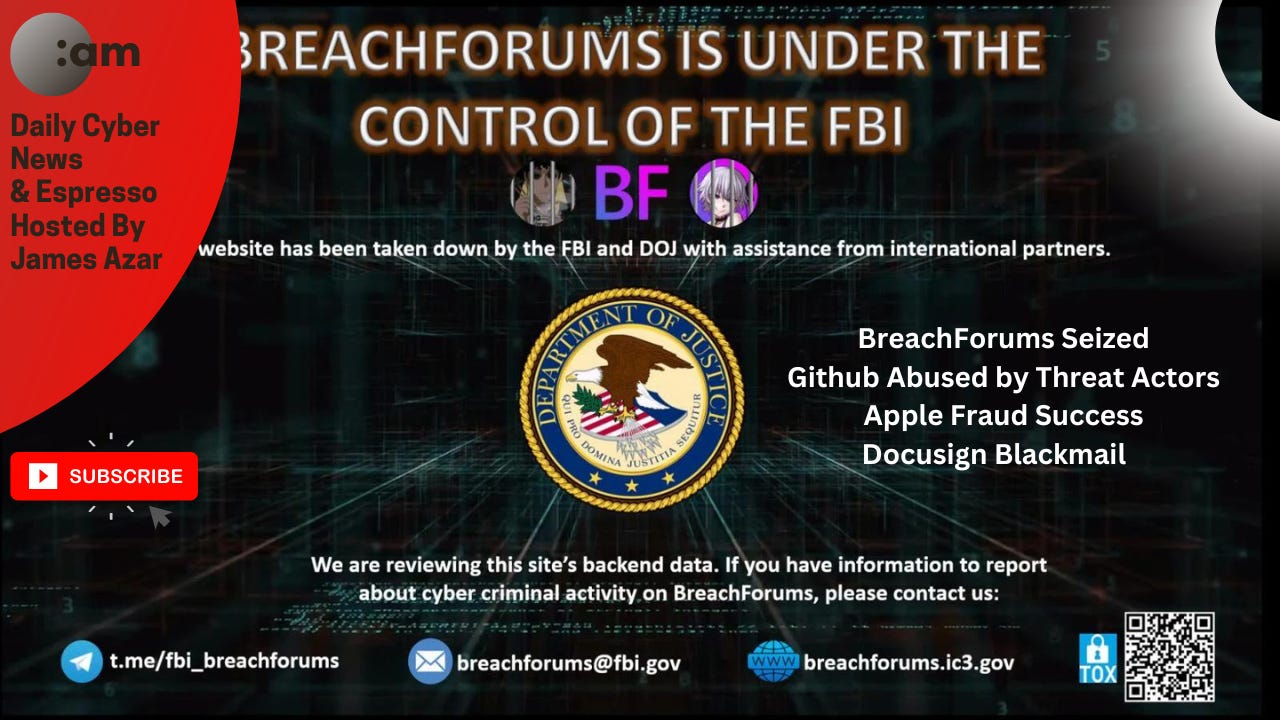
FBI Seizes BreachForum
The FBI, in collaboration with international partners, has seized the notorious BreachForum, known for leaking stolen corporate data. The site is now under FBI control, potentially providing valuable insights into cybercriminal activities.
Action Points:
Monitor Communications: Check for any breach-related notifications from law enforcement if your data might be involved.
Report Suspicious Activity: Contact the FBI with any information about cybercriminal activities linked to BreachForum.
Ransomware Hits Wichita and Other Cities
The city of Wichita, Kansas, faces ongoing challenges from a ransomware attack that compromised sensitive law enforcement information. Similar attacks have affected St. Helena, California, and Macon County, Georgia.
Action Points:
Enhance Security Measures: Review and strengthen cybersecurity protocols to protect against ransomware.
Stay Informed: Follow updates from local authorities regarding the status of affected systems and data breaches.
Intel's Massive Patch Tuesday Release
Intel has issued updates addressing 90 vulnerabilities, including a critical flaw in its neural compressor AI product. The updates span various products, emphasizing the importance of timely security patching.
Action Points:
Apply Patches: Ensure all Intel products are updated with the latest security patches.
Review Vulnerabilities: Assess the impact of identified vulnerabilities on your systems and take appropriate action.
GitHub Profile Abused to Spread Malware
A malicious campaign is using a legitimate GitHub profile to distribute information-stealing malware targeting macOS applications. The campaign is linked to a Russian-speaking threat actor.
Action Points:
Verify Software Sources: Only download applications from trusted and verified sources.
Monitor for Malware: Implement robust monitoring tools to detect and mitigate malware infections.
Apple's Fight Against Fraud
Apple has prevented over $7 billion in fraudulent transactions and blocked millions of stolen credit cards and fraudulent accounts. Their stringent app review process has rejected numerous malicious apps.
Action Points:
Stay Vigilant: Regularly review and update your security settings on Apple devices.
Report Fraud: Immediately report any suspicious activity on your Apple accounts.
Increase in Phishing Attacks Mimicking DocuSign
Researchers have noted a rise in phishing attacks that imitate DocuSign requests, leveraging templates from underground marketplaces to deceive victims.
Action Points:
Educate Employees: Train employees to recognize and avoid phishing scams.
Implement Verification Processes: Use multi-factor authentication and other verification methods for sensitive transactions.
Boost in Security Budgets Anticipated
A KPMG study reveals that security operations budgets are expected to increase by 20% over the next two years, driven by new regulations and heightened security needs.
Action Points:
Plan Ahead: Allocate budget increases effectively to address the most critical security gaps.
Stay Compliant: Ensure compliance with evolving security regulations to avoid penalties.
EU's Struggle with Spyware Regulation
The EU faces challenges in regulating spyware due to a lack of political will, as highlighted in a recent conference on the issue.
Action Points:
Advocate for Stronger Regulations: Support initiatives calling for stricter controls on spyware use.
Enhance Personal Security: Use privacy-enhancing technologies to protect against spyware.
LogRhythm and Exabeam Merger
LogRhythm and Exabeam, two major players in the Security Information and Event Management (SIEM) space, are merging to enhance their capabilities in threat detection and response.
Action Points:
Evaluate Impact: Assess how the merger might affect existing SIEM solutions and support.
Leverage New Capabilities: Explore new features and improvements offered by the combined entity.
Closing Remarks:
Thank you for joining us today. Remember to subscribe to our channel and check out our Substack for more updates. Stay cyber safe!
Upcoming Event:
Join us tomorrow at 11 a.m. as Chris Foulon and I discuss cybersecurity frameworks, featuring CIS Top 20 and the NIST framework. Don't miss it!
✅ Story Links:
https://therecord.media/law-enforcement-data-stolen-wichita-ransomware
https://www.securityweek.com/intel-publishes-41-security-advisories-for-over-90-vulnerabilities/
https://www.securityweek.com/threat-actors-abuse-github-to-distribute-multiple-information-stealers/
https://www.cybersecuritydive.com/news/cyber-security-operations-center-budget-SOC/716072/
https://therecord.media/eu-failure-spyware-political-will
https://www.securityweek.com/thoma-bravo-owned-logrhythm-announces-merger-with-rival-exabeam/
🔔 Subscribe now for the latest insights from industry leaders, in-depth analyses, and real-world strategies to secure your digital world. https://www.youtube.com/@TheCyberHubPodcast/?sub_confirmation=1
✅ Important Links to Follow:
👉Website:
👉Substack:
👉Listen here: https://linktr.ee/cyberhubpodcast
✅ Stay Connected With Us.
👉Website:
👉Rumble: https://rumble.com/c/c-1353861
👉Facebook: https://www.facebook.com/CyberHubpodcast/
👉Linkedin: https://www.linkedin.com/company/cyberhubpodcast/
👉Twitter (X): https://twitter.com/cyberhubpodcast
👉Instagram: https://www.instagram.com/cyberhubpodcast
✅ For Business Inquiries: info@cyberhubpodcast.com
=============================
✅ Other Videos You Might Be Interested In Watching:
👉 My thoughts on Israel from this morning's episode and the current state of cybersecurity attacks
👉 A Deep Dive into the MGM Resorts Ransomware - An Inside look into the current FACTS
👉 The Latest on the MGM Resorts Ransomware Attack & its impact on Vegas and Cybersecurity overall
👉 What Does Omer Adam & Tel Aviv have to do with Cybersecurity? Find out on CISO Talk
👉 Iran is targeting Israel using its proxies that are Hamas & Hizballah & using cyber-warfare
=============================
✅ About The CyberHub Podcast.
The Hub of the Infosec Community.
Our mission is to provide substantive and quality content that’s more than headlines or sales pitches. We want to be a valuable source to assist those cybersecurity practitioners in their mission to keep their organizations secure.
Tune in to our series of podcasts that provide everything from highlighting CISO in our CISOTalk Podcast or our signature CyberHub Podcast giving you the latest news live daily.














Share this post